An error in Microsoft Windows prior to Windows 10 when processing access to the root $ MFT file in the root directory may cause the system to crash. This can be exploited by attackers to trigger a denial-of-service. The $ MFT file is used by the NTFS file system to store metadata. The access to this file is normally only for the operating system itself. Access attempts to this file by users are usually blocked, however, if a user tries to access this file as a directory, for example, using “c: \ $ MFT \ 123”, NTFS blocks the file and does not release it. All other operations that access the file system must wait for the file to be released. This leads to a system blockage or to a complete system crash. According to current knowledge, Windows 10 is not affected by this problem*.
Testing
The bug was tested within my test environment using an un-patched Windows 7 machine, SP1. Results were the same when testing a default administrator and default user account. Below are the findings of the test:
Local Testing On Machine
Direct access to the link via Windows Explorer does not appear to crash the machine, instead displays an error
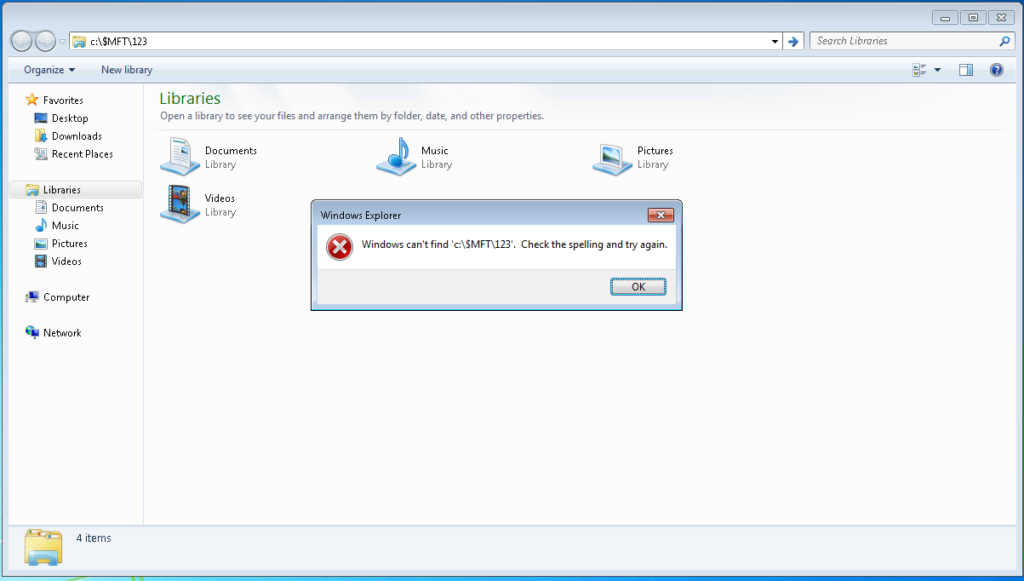
Running the command through a run terminal crashes the system completely. Restarting the machine seems to bring it back with no lasting affects seen again once the machine has been rebooted.
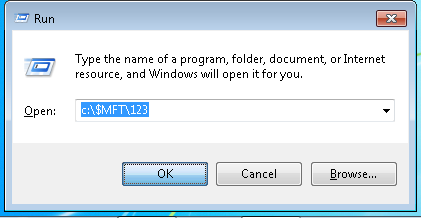
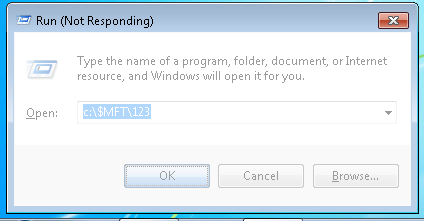
Web Browser Test
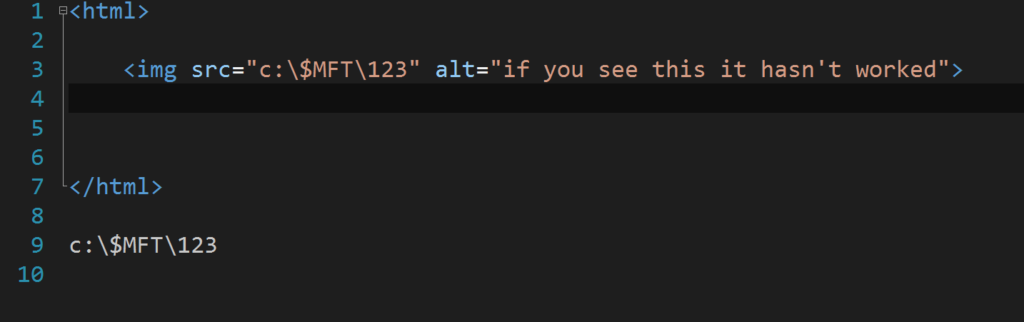
For this test the aim was to attempt to get the browser to retrieve the metadata file, using the html image tag. The source was set as the path for the NTFS metadata file with an alt tag used to display if the browser ignored the file. This was to test if this bug could be exploited remotely in the different browsers.
This is the code that was used:
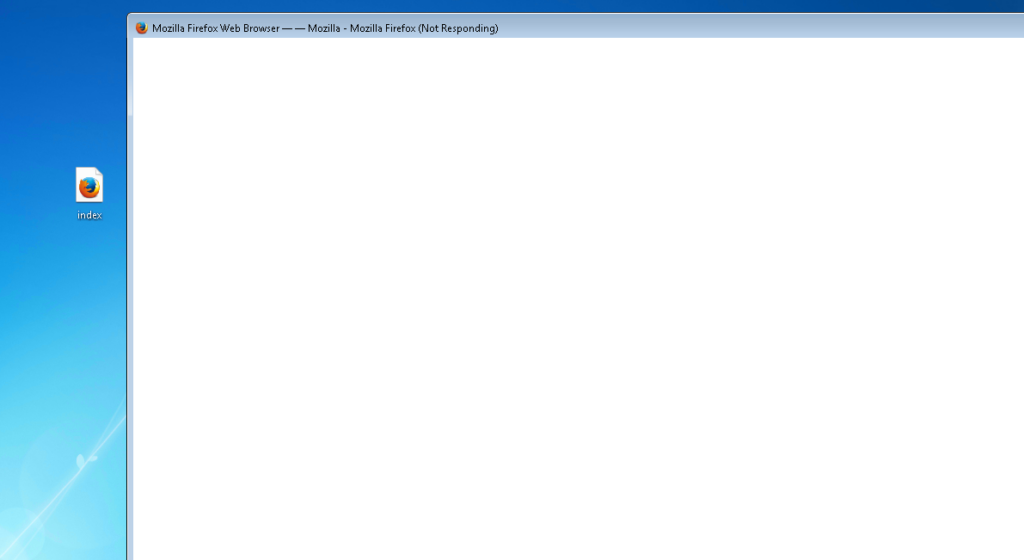
FireFox (v 53.0.3):
Complete browser lockup. Cannot even force to close via task manager. After time the system becomes unresponsive. Restarting the machine seems to bring it back with no lasting affects seen again once the machine has been rebooted.
Chrome (v 58.0.3029.110):
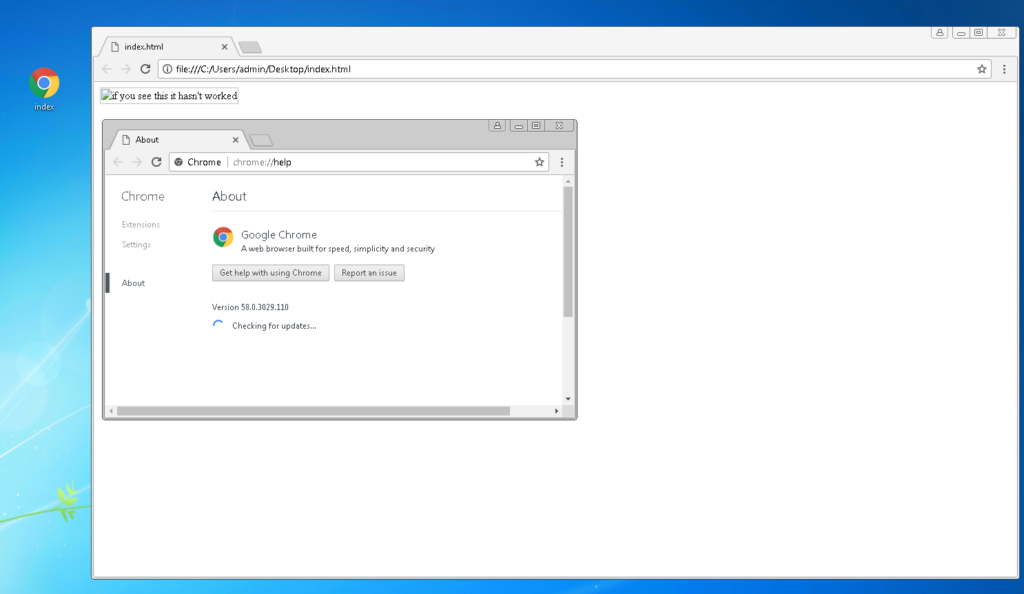
Does not display image, alt text appears, does not seem to be affected.
Windows 10 Testing
Although information available on the internet suggests that Windows 10 isn’t affected, the bug was tested on Windows 10 (10.0.10586 Build 10586) anyway. The command was run through a run terminal where no affects were seen. Although, when attempting to create an email in Outlook (2013) using the html code highlighted above the system locked up showing that Windows 10 might not be affected if the directory is directly searched but the bug does affect Windows 10 if the html code is rendered in some way. This was further proved true when opening the html file in Internet Explorer, with the system completely locking and needing a hard restart in order to gain back control.
Summary
The tests above show the bug not only affects Windows 7 systems but also windows 10 devices, rendering the machine unresponsive until the system is restarted. The bug can be exploited on remote devices provided the code in question is rendered on the system in some way (either via email or a browser style attack as shown above). Until a patch is released by Microsoft the standard security procedures should be followed and browsing on the internet on a critical system should not be performed. Furthermore, from tests conducted above it is clear to see that Chrome does not appear to be affected by the bug and should be used where possible. From the tests conducted it was observed no lasting damage could be seen on the machine but there is understandably a potential for huge disruptions to occur until the bug is patched by Microsoft.
Mitigation
- Use Chrome if and were possible, as it does not appear to affect this browser
- To follow standard security procedures and not to browse the internet or read emails on critical systems
- Microsoft has been informed, but have not disclosed if or when the problem will be patched.
